Some time ago i wrote up a post (located here) explaining how you can setup traffic manager with ADFS and have proper monitoring of the service. Today i will go over how to setup ADFS behind the Azure Application Gateway. This will enable you to protect your ADFS service and monitor it with the WAF provided by the application gateway.
Before we begin one prerequisite which i am still not sure if its really needed but i had problems and i believe this fixed it:
You need to set the default HTTPS Binding, i believe this is required as i am not sure if the health probe is truly SNI compliant, i might be wrong here but it doesn’t hurt to set this. To set it you simply need to run the following command on the WAP servers (just change the cert hash):
|
1
|
netsh http add sslcert ipport=0.0.0.0:443 certhash=xxxxxxxxxxxxxx appid={5d89a20c-beab-4389-9447-324788eb944a}
|
Ones that’s done create a Application gateway in Azure and do the following:
- Create a Frontend listener with thew following settings:
- HTTPS Protocol
- Listen on port 443
- Multi-Site type, you can do basic but that will limit your application gateway to only the ADFS service for port 443
- Provide a PFX file of your ADFS certificate. make sure you include the private key and a strong password
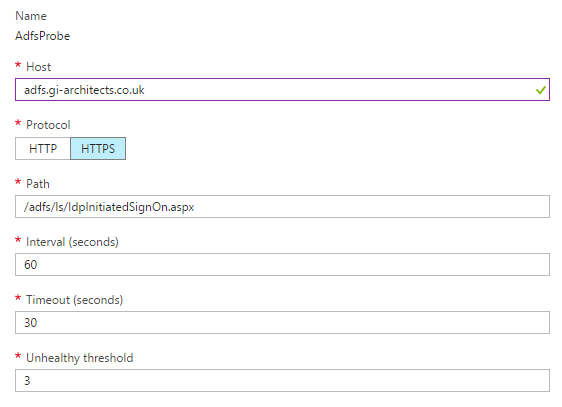
- Create a Health Probe with thew following settings (just change the host):
- Create a HTTP Setting with thew following settings
- HTTPS Protocol
- Cookie based affinity: Disabled (you really don’t need that for ADFS)
- Port 443
- Export your ADFS certificate as a base 64 format (do not include the private key) and add it.
- Tick the “Custom probe” and select the probe we created earlier
- Create a Backendpool which includes all your WAP servers
- Crete a Basic Rule using the objects created earlier.
And that’s it, this is not only a secure solution but it will give you a proper monitoring of both the WAP and ADFS servers. Works great with loadbalancing between on-prem and Azure.

Thanks for writing this up. I’m not having any luck with this unfortunately. Backend Health is reporting unhealthy for both hosts but they work fine behind a Load Balancer. I even adjusted the Application Gateways minimum SSL/TLS settings and made sure to set a custom cipher suite that matched our ADFS WAPs. No love :-\
Will report back once I get this working. Any suggestions welcomed.
Got this working FYI. That first netsh command is critical (must be run in elevated command prompt not PS) even if you already see the same cert thumbprint in your bindings. Also, we had hardened our our ADFS WAPs so we had to setup out Application Gateway’s custom SSL policy. Cheers!
https://docs.microsoft.com/en-us/azure/application-gateway/application-gateway-ssl-policy-overview