Microsoft has a very nice post on how to setup Traffic manager in front of an ADFS farm for high availability, where both sites are in Azure but in different GEO locations or one in Azure and one on premises. The Article is located here: https://docs.microsoft.com/en-us/azure/active-directory/active-directory-adfs-in-azure-with-azure-traffic-manager. What the article lacks is how to setup proper ADFS monitoring, which monitors both tte WAP and the ADFS service, at the moment the article only goes into details which monitor the WAP service.
So this post will go over how to configure your environment so the health point will report the status of both WAP and ADFS.
Some info before we begin:
- The solutions is achieved by monitoring the /adfs/probe/ on the ADFS server via the WAP proxy
- The solution will report failure if the WAP proxy is not forwarding or the ADFS service is down. So we are monitoring the whole solution.
- It will work if you have an external load balancer in front of the WAP servers and an internal one in front of the ADFS servers, for simplicity I will outline how it’s done on the non-load-balanced solution but it’s the same procedure for both.
- You can’t monitor /adfs/probe on the WAP server as that will only give you the status of the WAP server
- You can create a rule on the WAP server to redirect /adfs/probe to the ADFS server, but it will get ignored and show you the status of the WAP server.
- I tested this on Server 2016 but it will work for 2012 R2 as well
- If you are using 2012 R2 make sure you update your WAP to the latest version so you can forward HTTP traffic
- We use HTTP as this prevents certificate problems and because Traffic manager does not support SNI.
- You can’t monitor the “/federationmetadata/2007-06/federationmetadata.xml” because the way you set this up for Traffic manager means you are monitoring the ADFS on a different DNS so the request will not be forwarded.
Essentially this is what we are doing
Once you setup the environment as per Microsofts Article above we need to do the following:
The variables for my test environment:
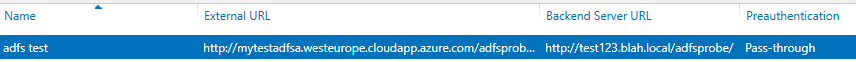
- ADFS URL and Federation Service Name – test123.blah.local
- Traffic Manager DNS – adfstest.trafficmanager.net
- WAP server public IP dns (this can be replaced by a load balancer) – http://mytestadfsa.westeurope.cloudapp.azure.com
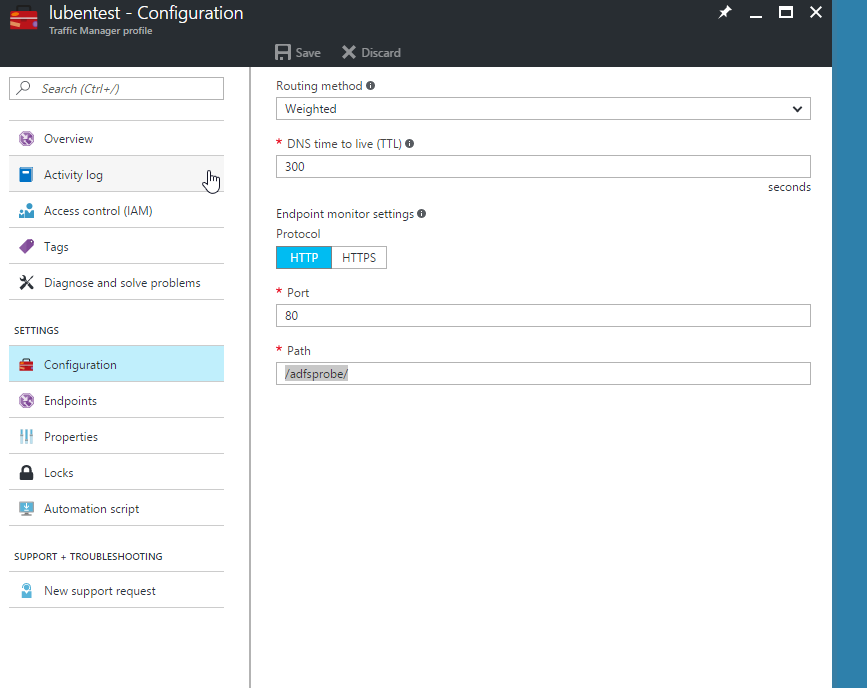
- Custom monitor path (you can choose anything but the default which is /adfs/) – /adfsprobe/
The Steps:
- Change the Traffic Manager Configuration to point to our custom monitor path for the endpoint monitoring
- Create an HTTP rule on the WAP server in the Remote Access Management Console to forward (via Pass- through) the WAP DNS + our custom monitor path to the ADFS server. I assume that your WAP server host file has been modified to point the ADFS URL to the ADFS internal IP or load balancer IP
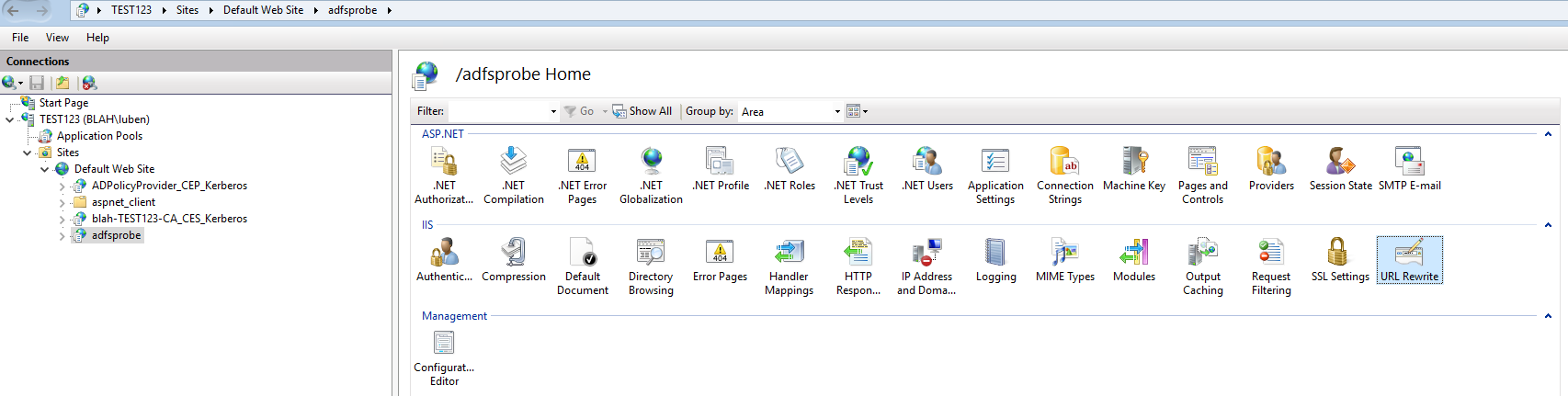
- Install IIS (it’s usually installed by default with ADFS) + URL Rewrite (https://www.iis.net/downloads/microsoft/url-rewrite) + Application Request Routing (https://www.iis.net/downloads/microsoft/application-request-routing) on the ADFS server.
- Create a new application under the Default Web Site call it the same name you used for your custom monitor path nd then create a new URL Rewrite Rule
- The rule to be created is Reverse Proxy with the following settings:
- And finally change your Public DNS record and create a CName for your ADFS URL (test123.blah.local) to point to the traffic manager DNS name (adfstest.trafficmanager.net)
And you are done.