While setting up gitlab with ADFS 3.0 we noticed there is a couple of gotchas you need to watch out for:
- You need to set the NotBeforeSkew to something like 2 in ADFS
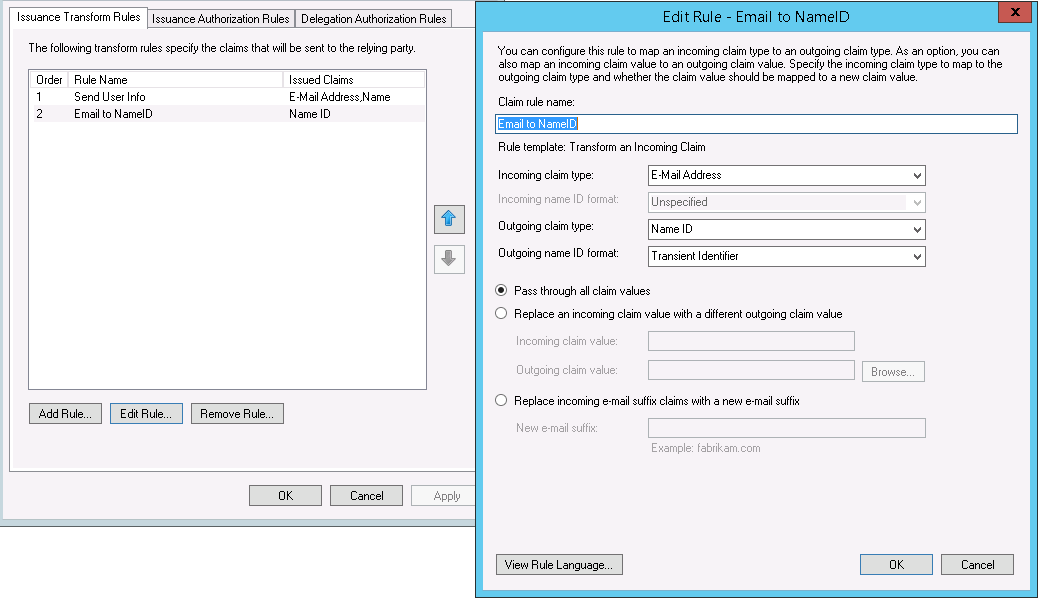
- You need to trasform the transient identifier in ADFS
- idp_cert_fingerprint is case sensitive and needs to be all in CAPS
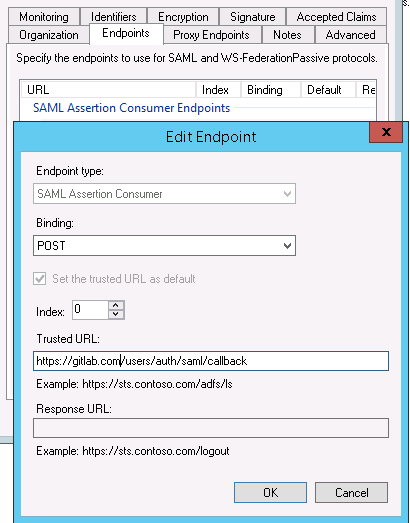
To set it up follow the following instructions:
In gitlab you need to set the following config
- Replace the https://gitlab.com with your gitlab address
- Replace the https://adfs.com with your ADFS address
- REplace the https://gitlab.local with what ever you like
- Replace 35:FA:DD:CF:1E:8F:8B:E4:CA:E1:AE:2A:EF:70:95:D5:DC:5C:67:1B with the finger print of your signing certificate
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
|
gitlab_rails['omniauth_enabled'] = true
gitlab_rails['omniauth_allow_single_sign_on'] = ['saml']
gitlab_rails['omniauth_auto_sign_in_with_provider'] = 'saml'
gitlab_rails['omniauth_block_auto_created_users'] = false
gitlab_rails['omniauth_auto_link_ldap_user'] = true
gitlab_rails['omniauth_auto_link_saml_user'] = true
gitlab_rails['omniauth_providers'] = [
{
"name" => "saml",
"args" => {
assertion_consumer_service_url: 'https://gitlab.com/users/auth/saml/callback',
idp_cert_fingerprint: '35:FA:DD:CF:1E:8F:8B:E4:CA:E1:AE:2A:EF:70:95:D5:DC:5C:67:1B',
idp_sso_target_url: 'https://adfs.com/adfs/ls/',
issuer: 'https://gitlab.local',
attribute_statements: { email: ['http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress'] },
name_identifier_format: 'urn:oasis:names:tc:SAML:2.0:nameid-format:transient'
}
}
]
|
For ADFS configure the following settings (Use the same address replacements as above):
Then Run the following command to set the skew in Powershell on the ADFS server:
|
1
|
Set-AdfsRelyingPartyTrust -TargetIdentifier "Gitlab Trust" -NotBeforeSkew 2
|